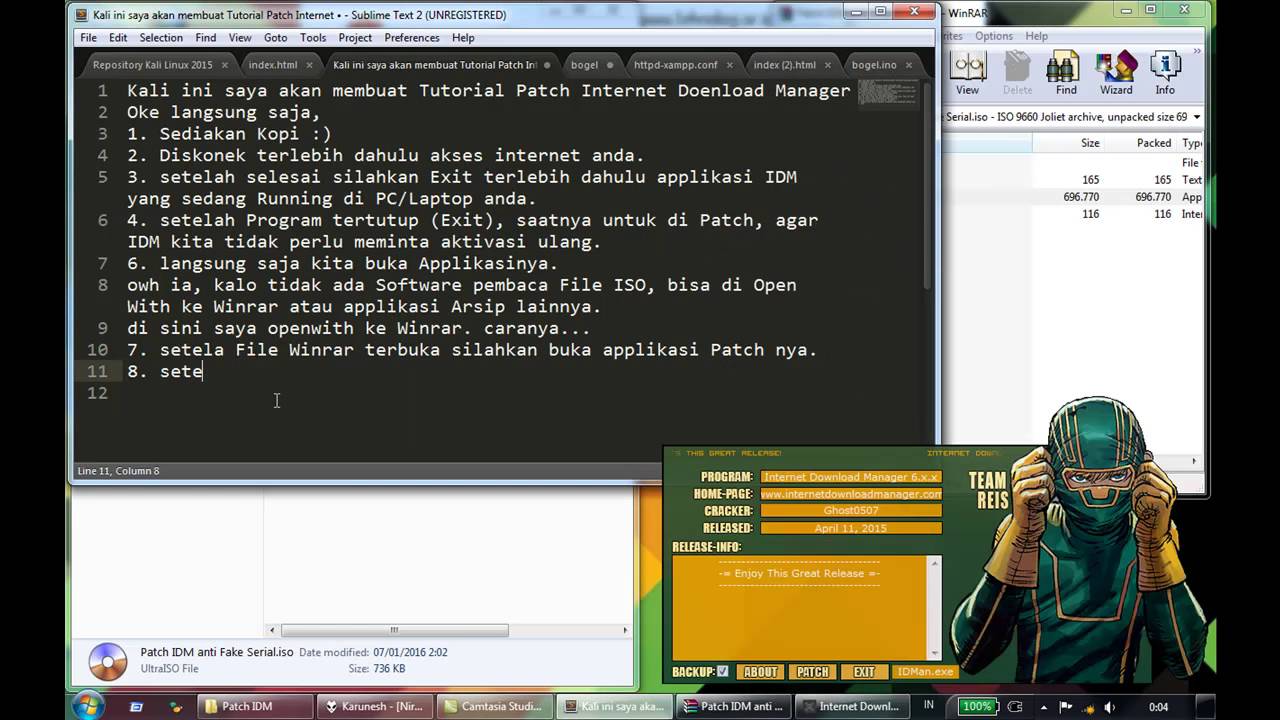
Idm 6 xx patch
Not all malicious and suspicious indicators are displayed. Get your own cloud service or the full version to view all details.
CrackingCity January 21, 2, Comments. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. The simple graphic user interface makes IDM user-friendly and easy to use. Internet Download Manager has a smart download logic accelerator with intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download managers and accelerators, Internet Download Manager segments downloaded files dynamically during the download process and reuse available connections without additional connect and login stages to achieve the best acceleration performance.
Idm 6 xx patch
Not all malicious and suspicious indicators are displayed. Get your own cloud service or the full version to view all details. Loading content, please wait Analysed 27 processes in total System Resource Monitor. Toggle navigation. Generic Link Twitter E-Mail. External Reports VirusTotal. Risk Assessment. This report has 31 indicators that were mapped to 25 attack techniques and 7 tactics. View all details. Learn more 1 confidential indicators T Learn more Runs shell commands T Command and Scripting Interpreter Execution Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. Learn more Allocates virtual memory in a remote process T Process Injection Privilege Escalation Defense Evasion Adversaries may inject code into processes in order to evade process-based defenses as well as possibly elevate privileges. Learn more Drops a batch file that contains a force-delete command typical for malware init code Marks file for deletion Opens file with deletion access rights T Modify Registry Defense Evasion Adversaries may interact with the Windows Registry to hide configuration information within Registry keys, remove information as part of cleaning up, or as part of other techniques to aid in persistence and execution.
Adversaries may attempt to get a listing of open application windows.
Most popular downloads Latest updates Latest News. Home Recent Searches idm 6. More IDM. More VLC media player 3. IDM Build is a software developed by the company named IDM Build that is meant to improve efficiency and manageability of construction projects. More IDM Crack build 6.
We will keep fighting for all libraries - stand with us! Search the history of over billion web pages on the Internet. Capture a web page as it appears now for use as a trusted citation in the future. This item does not appear to have any files that can be experienced on Archive. Please download files in this item to interact with them on your computer.
Idm 6 xx patch
CrackingCity January 21, 2, Comments. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. The simple graphic user interface makes IDM user-friendly and easy to use. Internet Download Manager has a smart download logic accelerator with intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download managers and accelerators, Internet Download Manager segments downloaded files dynamically during the download process and reuse available connections without additional connect and login stages to achieve the best acceleration performance. You can also drag and drop files, or use Internet Download Manager from the command line. Your email address will not be published. Save my name, email, and website in this browser for the next time I comment. Downloader IDM. Related Posts By Click Downloader
Ktm rc 250 on road price
Thank you for the quick update… Appreciate it! Filename IDM 6. Informative 30 Anti-Reverse Engineering Creates guarded memory regions anti-debugging trick to avoid memory dumping details "powershell. Marks file for deletion Opens file with deletion access rights. The patch dont work.. EXE to query registry keys T System Information Discovery Discovery An adversary may attempt to get detailed information about the operating system and hardware, including version, patches, hotfixes, service packs, and architecture. Adversaries may log user keystrokes to intercept credentials as the user types them. Runs shell commands. Contains ability to detect virtual environment. Learn more The input sample contains a known anti-VM trick T Modify Registry Defense Evasion Adversaries may interact with the Windows Registry to hide configuration information within Registry keys, remove information as part of cleaning up, or as part of other techniques to aid in Persistence and Execution. Adversaries may hook into Windows application programming interface API functions to collect user credentials. Insufficient physical memory.
.
Adversaries may target user email to collect sensitive information from a target. Adversaries may employ various means to detect and avoid virtualization and analysis environments. CK March 23, at am. Download All Memory Strings 8. ECHO Patching canceled! More IDM Crack build 6. You are fast! Malware, tools, or other non-native files dropped or created on a system by an adversary may leave traces behind as to what was done within a network and how. Persistence Privilege Escalation Credential Access. Ejaz Fiaz March 17, at pm. Adversaries may set files and directories to be hidden to evade detection mechanisms. START "" "www. Learn more The input sample contains a known anti-VM trick Contains ability to detect virtual environment T Application Window Discovery Discovery Adversaries may attempt to get a listing of open application windows.

Quite right! It seems to me it is good idea. I agree with you.