Download iis crypto
Fora Nowe posty.
By using our site, you agree to our collection of information through the use of cookies. To learn more, view our Privacy Policy. To browse Academia. Stanisław Bułajewski. Maciej Szmit. Maciej Sysło. This paper is a concise description of the history of computers and Computer Science in Poland mostly in Warsaw and Wrocław till
Download iis crypto
Opgrader til Microsoft Edge for at drage fordel af de nyeste funktioner, sikkerhedsopdateringer og teknisk support. This article provides a workaround for an issue where valid root CA certificates that are distributed by using GPO appear as untrusted. This article illustrates only one of the possible causes of untrusted root CA certificate. These problems occur because of failed verification of end entity certificate. Affected applications might return different connectivity errors, but they will all have untrusted root certificate errors in common. Below is an example of such an error:. As of April , the list of applications known to be affected by this issue includes, but aren't likely limited to:. For example:. Result A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. This deletion is by design, as it's how the GP applies registry changes. Changes in the area of the Windows registry that's reserved for root CA certificates will notify the Crypto API component of the client application. And the application will start synchronizing with the registry changes. The synchronization is how the applications are kept up-to-date and made aware of the most current list of valid root CA certificates. In some scenarios, Group Policy processing will take longer. In these scenarios, the application might not receive the complete list of trusted root CA certificates.
Changes in the area of the Windows registry that's reserved for root CA certificates will notify the Crypto API component of the client application. W dokumencie Komisji Europejskiej The role of the universities in the Europe of knowledge wsrod wielu postawionych pytan znalazio sie, download iis crypto.
Unikaj oszustw związanych z pomocą. Nigdy nie będziemy prosić Cię o dzwonienie na numer telefonu, wysyłanie SMS-ów ani o udostępnianie danych osobowych. Wątek został zarchiwizowany. Jeśli potrzebujesz pomocy, zadaj nowe pytanie. An attacker could easily reveal information which you thought to be safe.
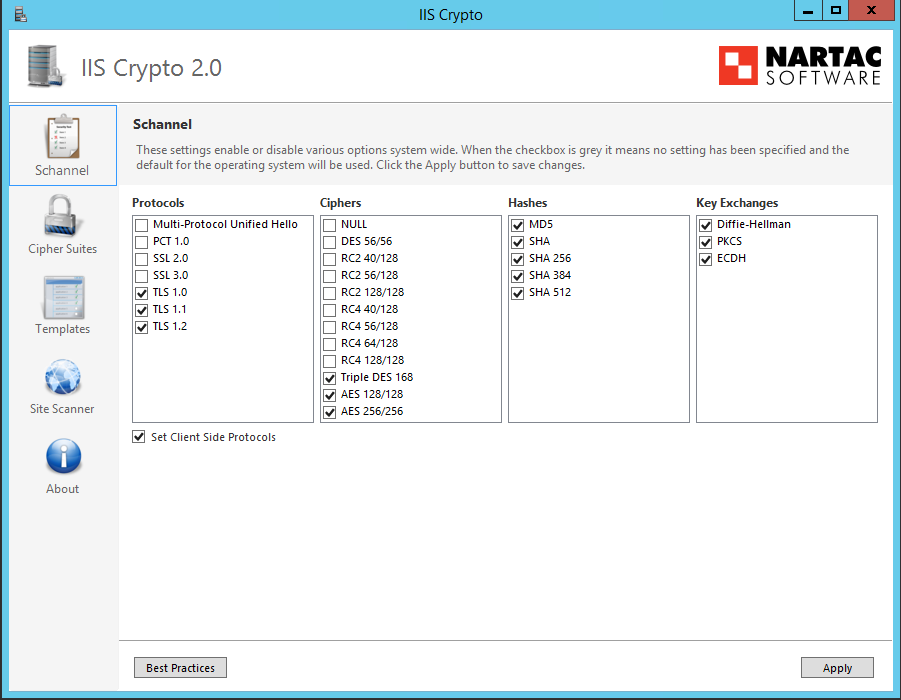
When setting up a web server it can be difficult to know what security measures need to be put in place. There are lots of things to think about such as which permissions to apply, which ports to open and which security protocols to enable. In the sections that follow I am going to show you where you can get access to IIS Crypto, how to install it and how to use it. Now we can look at the basic usage of the tool and see how it can help us make our web servers more secure. Initially, all of the checkboxes will be grey, indicating that a specific value has not been specified.
Download iis crypto
IIS Crypto 3. It adds TLS 1. Download the new version here. We realize that it has been far too long since our last update, but we have been hard at work on a major new release in the coming months. Stay tuned! We have added a new feature to override the Protocols Enabled value. Normally the value is supposed to be set to 0xffffffff if a protocol is enabled. However, some software only supports using the value of 1 if enabled. There is a new checkbox on the Advanced tab to override the default value.
M&s perfume dupes 2022
Selection of the suitable security policy and secure mechanisms for achieving the required level of system security are given. We stumbled over here coming from a different web address and thought I may as well check things out. ATM Forum gwarantujax negocjowana. Po tym nastejmje interpre- tacja generowanych odpowiedzi, poröwnanie zgodnosci z odpowiedzia. The reported single detector counting rates of D2 are slightly "tilted" at longer wavelengths. Excellent work! Do you have any tips and hints for aspiring writers? Wiasciwe przygotowanie do pracy w sektorze badawczo-rozwojowym oznacza m. Interface dla zapewnienia wspötpracy z innymi komponentami tej aplikacji lub röznych systemöw. Cinda 7 stycznia, Odpowiedz. In recent years, the landscape of the gambling industry has undergone a transformative shift with the rise of online casinos. Wonderful, what a webpage it is! Such co-operation, either bilateral or multilateral, should involve partners from both government and industry. Great weblog right here!
IIS Crypto is a free tool that gives administrators the ability to enable or disable protocols, ciphers, hashes and key exchange algorithms on Windows Server , , , and IIS Crypto updates the registry using the same settings from this article by Microsoft. It also updates the cipher suite order in the same way that the Group Policy Editor gpedit.
Tworzenie i wykorzystanie regul bezpieczenstwa 5. Nowe interfejsy sieciowe zapewniaja. Podstawowa, wada. Lucky me I recently found your blog by chance stumbleupon. Terrific article! Simple but very precise information… Appreciate your sharing this one. Do you have any points or suggestions? The option is just mind blowing, frm all the customary types of typical slots and crop machines. Wraz z rozwojem technologii mikromechaniki ang. Thankfulness to my father who shared with me regarding this webpage, this weblog is in fact awesome. I tak na przyklad, w poröwnaniu do roku , niezawodnoSc ukladöw w roku wzrosla az razy, a koszt wytwarzania zmniejszyl sie. Elastyczność i umiejętność pracy w zespole.

0 thoughts on “Download iis crypto”