Which security related phrase relates to the integrity of data
Integrity means that any data is stored and transferred as intended and that any modification is authorized. Integrity is part of the CIA triad. Information is accessible only to those authorized to view or modify it.
How might the goals of a basic network management not be well-aligned with the goals of security? A company has an annual contract with an outside firm to perform a security audit on their network. The purpose of the annual audit is to determine if the company is in compliance with their internal directives and policies for security control. Select the broad class of security control that accurately demonstrates the purpose of the audit. A Managerial is the control that gives oversight of the information system including selection of other security controls.
Which security related phrase relates to the integrity of data
This specification describes mechanisms for ensuring the authenticity and integrity of Verifiable Credentials and similar types of constrained digital documents using cryptography, especially through the use of digital signatures and related mathematical proofs. This section describes the status of this document at the time of its publication. The Working Group is actively seeking implementation feedback for this specification. In order to exit the Candidate Recommendation phase, the Working Group has set the requirement of at least two independent implementations for each mandatory feature in the specification. For details on the conformance testing process, see the test suites listed in the implementation report. A Candidate Recommendation Draft integrates changes from the previous Candidate Recommendation that the Working Group intends to include in a subsequent Candidate Recommendation Snapshot. This is a draft document and may be updated, replaced or obsoleted by other documents at any time. It is inappropriate to cite this document as other than work in progress. This document was produced by a group operating under the W3C Patent Policy. W3C maintains a public list of any patent disclosures made in connection with the deliverables of the group; that page also includes instructions for disclosing a patent. An individual who has actual knowledge of a patent which the individual believes contains Essential Claim s must disclose the information in accordance with section 6 of the W3C Patent Policy.
The algorithms defined below operate on documents represented as JSON objects. We specifically use the value of unsecuredDocument as set above, rather than using the value from step 5 of the algorithm in section 4.
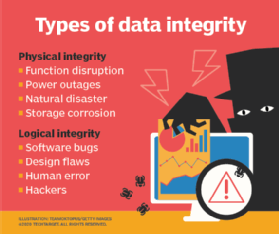
Biba in , [1] is a formal state transition system of computer security policy describing a set of access control rules designed to ensure data integrity. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not corrupt data in a level ranked higher than the subject, or be corrupted by data from a lower level than the subject. In general the model was developed to address integrity as the core principle, which is the direct inverse of the Bell—LaPadula model which focuses on confidentiality. This security model is directed toward data integrity rather than confidentiality and is characterized by the phrase: "read up, write down". This is in contrast to the Bell-LaPadula model which is characterized by the phrase "read down, write up".
Information security relies on keeping data secure, integral, and available—but tradeoffs are necessary in real-world scenarios. The model has nothing to do with the U. Central Intelligence Agency; rather, the initials stand for the three principles on which infosec rests:. These three principles are obviously top of mind for any infosec professional. But considering them as a triad forces security pros to do the tough work of thinking about how they overlap and can sometimes be in opposition to one another, which can help in establishing priorities in the implementation of security policies. Ben Miller, a VP at cybersecurity firm Dragos, traces back early mentions of the three components of the triad in a blog post; he thinks the concept of confidentiality in computer science was formalized in a U. Air Force study , and the idea of integrity was laid out in a paper that recognized that commercial computing in particular had specific needs around accounting records that required a focus on data correctness.
Which security related phrase relates to the integrity of data
Data integrity refers to the accuracy and consistency of data over its lifecycle. Without accurate information, companies are not able to use it in any way. Data integrity can be compromised and checked for errors. Validation procedures are used to ensure the data is not changed during transfer or replication. Schedule a demo to learn how we can help. Data integrity can mean one of two things: either the state that a data set is in, or it refers to processes used for accuracy. Error checking and validation methods are an example of this.
Bask and stow
During verification, the transformation and hashing steps are conceptually the same as described above. Examples of transformations include canonicalization and binary-to-text encoding. Use arp to check the MAC addresses associated with those IP addresses and investigate possible spoofing. However, some combinations of cryptographic parameters might actually reduce security. This is either gray hat hacking or black hat hacking. The baseurl-no-pad alphabet is used to encode the bytes. Knowledge of the necessary secret makes it computationally easy to access certain information. Implementers are advised to consider these sorts of attacks when implementing defensive security strategies. First, they will check the proof with an id property whose value is urn:proof-1 against the public key of the VP of Engineering. Monitoring of risk and compliance is a type of managerial control, not an operational control. A meeting is scheduled with IT staff to brainstorm ideas for deploying security controls by category and function throughout the organization. For example, a cryptographic public key can be used as a verification method with respect to a digital signature; in such usage, it verifies that the signer possessed the associated cryptographic private key. Often the most appropriate technique for external assessment of the network perimeter or when performing web application scanning.
All Resources. Visit Blog. Read Report.
Loading flashcards This process is conceptually similar to how a phone address book functions, where one takes a person's name the input data and maps that name to that individual's phone number the hash. Add a note indicating that selective disclosure proof mechanisms can be compatible with Data Integrity; for example, an algorithm could produce a merkle tree from a canonicalized set of N-Quads and then sign the root hash. Keyloggers are spyware. This section describes the status of this document at the time of its publication. Weak encryption vulnerabilities allow unauthorized access to data. If the author of a message wishes it to be selectively disclosable by its recipient, then they need to enable selective disclosure on the specific message, and both need to use a capable cryptosuite. After a poorly handled security breach, a company updates its security policy to include an improved incident response plan. The capabilityInvocation verification relationship is used to specify a verification method that might be used by the controller to invoke a cryptographic capability, such as the authorization to update the controller document. The decoded binary data header is 0xed01 , which specifies that the remaining data is a byte raw Ed public key. The recommended naming convention for cryptographic suites is a string composed of a signature algorithm identifier, separated by a hyphen from an option identifier if the cryptosuite supports incompatible implementation options , followed by a hyphen and designation of the approximate year that the suite was proposed. There are at least two mechanisms that can provide some level of unlinkability.

I think, that you are not right. I am assured. I suggest it to discuss.