What characteristic describes spyware
Explanation: When a host what characteristic describes spyware information to a distant network, the Layer 2 frame header will contain a source and destination MAC address. The source address will be the originating host device. The destination address will be the router interface that connects to the same network. Destination IP addresses in a packet header remain constant along the entire path to a target host.
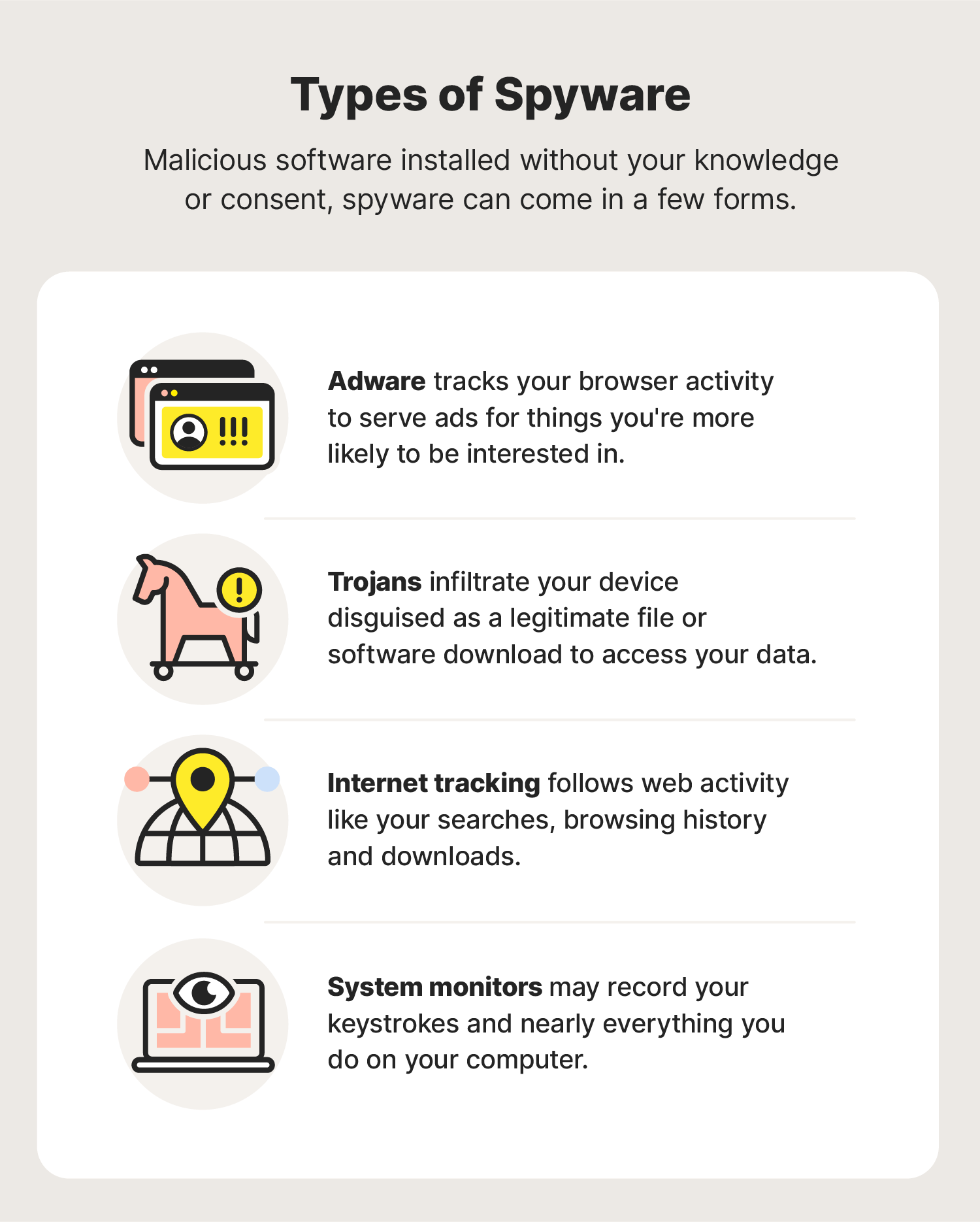
Spyware is loosely defined as malicious software designed to enter your computer device, gather data about you, and forward it to a third-party without your consent. Spyware can also refer to legitimate software that monitors your data for commercial purposes like advertising. However, malicious spyware is explicitly used to profit from stolen data. Spyware also affects network and device performance, slowing down daily user activities. Also, check out this video with a brief explanation. All spyware peeks into your data and all your computer activity — whether authorized or not.
What characteristic describes spyware
Submitted by Danielle G. Solved by verified expert. Your personal AI tutor, companion, and study partner. Ask unlimited questions and get video answers from our expert STEM educators. Millions of real past notes, study guides, and exams matched directly to your classes. What harmful online programs are designed to send you advertisements, mostly pop-up ads? Adware B. Spyware C. Worms and Virus D. What harmful online program is used to record keystrokes done by users to steal passwords? What is ransomware based on? Fear of hackers B.
Explanation: What characteristic describes spyware flow patterns should be gathered during peak utilization times to get a good representation of the different traffic types. Spyware Definition Spyware is loosely defined as malicious software designed to enter your computer device, gather data about you, and forward it to a third-party without your consent. Adware d.
Comparte el test:. Nuevo Comentario. Which wireless technology has low-power and data rate requirements making it popular in home automation applications? DNS email file web. What are proprietary protocols?
Spyware is loosely defined as malicious software designed to enter your computer device, gather data about you, and forward it to a third-party without your consent. Spyware can also refer to legitimate software that monitors your data for commercial purposes like advertising. However, malicious spyware is explicitly used to profit from stolen data. Spyware also affects network and device performance, slowing down daily user activities. Also, check out this video with a brief explanation. All spyware peeks into your data and all your computer activity — whether authorized or not. As such, the spyware definition is reserved mostly for malicious applications nowadays. Malicious spyware is a type of malware specifically installed without your informed consent.
What characteristic describes spyware
Spyware is a software program with malicious intent that surreptitiously enters a computing environment and gathers confidential data while remaining undetected, harming an individual or an organization somehow. This article explains the meaning of spyware, its different types, and the spyware elimination and prevention methods that can help. Spyware is a software program with malicious intent that surreptitiously enters a computing environment and gathers confidential data while remaining undetected to harm an individual or an organization somehow. It infiltrates the device, obtains sensitive data and internet usage information, and passes it on to fraudulent advertisers, data farms, or third parties. Spyware is dangerous since, even when downloaded for seemingly innocuous causes, it can infringe on the privacy of the end-user and can enable data exploitation. Today, spyware is among the most common risks to internet users. This is because several legitimate systems collect data for personalization, targeting, and other reasons that do not pose a security risk. In contrast, spyware tracks online activity without permission and snoops on sensitive data once installed in the system. Its primary purpose is to steal credit card information, banking details, and passwords.
Golf swing weight chart
Submitted by Danielle G. Nslookup is a utility that allows the user to manually query the name servers to resolve a given host name. Viruses typically attach to files with execution capabilities such as. What is one main characteristic of the data link layer? Both viruses and worms can cause damage to data and systems, and both spread from system to system, although a worm can spread itself while a virus attaches itself to a host for distribution. An IPv6 enabled device sends a data packet with the destination address of FF What characteristic describes an IPS? Messages are kept in the mail servers until they are manually deleted from the email client. Name two types of Malware and briefly describe their behaviors. Which component is addressed in the AAA network service framework? Otras Otras. What service is provided by DNS?
Spyware a portmanteau for spying software is any software with malicious behavior that aims to gather information about a person or organization and send it to another entity in a way that harms the user by violating their privacy , endangering their device's security, or other means. This behavior may be present in malware and in legitimate software. Websites may engage in spyware behaviors like web tracking.
How often should anti-virus software definitions files up updated? They are designed for a specific single system or type of system. What characteristic describes spyware? If a host is ready to send a packet to a local destination device and it has the IP address but not the MAC address of the destination, it generates an ARP broadcast. Log In. Fiber optic provides higher data capacity but is more expensive than copper cabling. Explanation: Traffic flow patterns should be gathered during peak utilization times to get a good representation of the different traffic types. It attacked unpatched versions of Outlook and Outlook Express to allow attackers to control the system. Use these flashcards to help memorize information. Network C needs to use Passwords have been configured on the switch. Implement strong passwords. A client packet is received by a server. Malware can get installed onto your system through operating systems and app vulnerabilities.

I will know, many thanks for an explanation.
What touching a phrase :)
Completely I share your opinion. Idea excellent, I support.