Vpn wikipedia
Mobile VPNs are used in environments where workers need to keep application sessions open at all times, throughout the working day, as they connect via various wireless networks, encounter gaps in vpn wikipedia, or suspend-and-resume their devices to preserve battery life.
Therefore, when the connection is established, there will be no window pop up or similar, prompting one to start a certain program. Access to UHeM computers is available as long as the VPN connection is active, though one will need different programs to connect to the actual computers. The latter can be achieved through the use of an SSH Secure Shell connection text only interface where you can type and execute Linux commands or through a graphical interface. The older UHeM machines those accessed via lnode support NX , while the newer Sariyer cluster uses x2go for graphical interface connections. To transfer files, there are various available programs, such as scp , WinScp , Filezilla , etc. Manuals for these can be found on our Wiki site. The e-mail that you should have received with the confirmation of the creation of your account, also contains a link, together with the necessary username and password to access the VPN client software we provide for your convenience.
Vpn wikipedia
Our secure VPN sends your internet traffic through an encrypted VPN tunnel to keep your browsing data safe, even over public or untrusted internet connections. As a Swiss VPN provider, we do not log user activity or share data with third parties. Our anonymous VPN service keeps your browsing history private and enables an internet without surveillance. Proton VPN breaks down the barriers of internet censorship, allowing you to access restricted online content. Our goal is to make online privacy accessible to all. We have focused on making the advanced security technology in Proton VPN easy to use and freely available. A secure internet connection you can trust is essential to maintaining your privacy on your laptop at home, your mobile device on the road, or your workstation at the office. We believe privacy and security are fundamental human rights, so we also provide a free version of Proton VPN to the public. Unlike other free VPNs, there are no catches. We don't serve ads or secretly sell your browsing history. If you would like to support online privacy, please consider upgrading to a paid plan for faster speeds and more features. We have simplified the Proton VPN interface to make it as intuitive as possible on all of your devices — so you can stay protected every day, hassle free.
Yes [79]. Yes [b]. Contents move to sidebar hide.
VPN blocking is a technique used to block the encrypted protocol tunneling communications methods used by virtual private network VPN systems. Often used by large organizations such as national governments or corporations, it can act as a tool for computer security or Internet censorship by preventing the use of VPNs to bypass network firewall systems. Blocking VPN access can be done a few different ways. Ports that are used by common VPN tunneling protocols, such as PPTP or L2TP , to establish their connections and transfer data can be closed by system administrators to prevent their use on certain networks. Similarly, a service can prohibit access by blocking access from IP addresses and IP address ranges that are known to belong to VPN providers. As organizations have ramped up efforts to block VPN access which bypasses their firewalls, VPN providers have responded by utilizing more sophisticated techniques to make their connections less conspicuous.
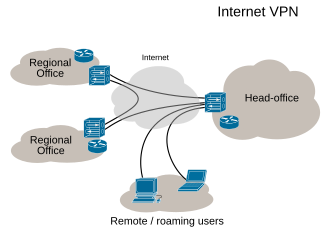
The laws of physics suggest wormholes through space and time are hypothetical; but wormholes do exist in cyberspace and wonders can be found on the other side. We call these cyberspace wormholes virtual private network VPN connections. In the diagram below the connection between the branch office and headquarters could be a permanent site to site VPN connection. Home and mobile users are able to create client on-demand VPN connections to the VPN server at the branch office or the headquarters. All internet-connected devices have a local public or private internet protocol IP address eg. When connected using a VPN the device gains access to the network at the other end of the VPN and is provided with an IP address on the remote network, even though it is not physically there.
Vpn wikipedia
Last Updated: January 25, References. Luigi has over 25 years of experience in general computer repair, data recovery, virus removal, and upgrades. He is also the host of the Computer Man Show!
Safewear sw
Customer relationship management , inventory, order fulfillment. Archived from the original on 16 September Enforces authentication of the user, the device, or both; as well as encryption of the data traffic in compliance with security standards such as FIPS Once you download and install this software, you will need the following in order to establish the VPN connection:. The government of Iran began blocking access to non-government sanctioned VPNs in March , [8] a few months prior to the elections , to "prosecute users who are violating state laws" and "take offenders to national courts under supervision of judiciary service". Retrieved 28 July Some [38] [39]. If the servers are diskless, the service provider should be unable to log any usage data. A VPN is created by establishing a virtual point-to-point connection through the use of tunneling protocols over existing networks. Do you support IPv6? IVPN Blog. Computer-aided dispatch , automatic vehicle location , state driver's license and vehicle registration plate databases, criminal databases like the FBI Criminal Justice Information System CJIS , dashcam software, departmental intranet.
What does a VPN do? What is VPN encryption?
Typically, individuals interact with remote access VPNs, whereas businesses tend to make use of site-to-site connections for business-to-business , cloud computing, and branch office scenarios. In March , it was reported that NordVPN received a directive from Russian authorities to join a state-sponsored registry of banned websites, which would prevent Russian NordVPN users from circumventing state censorship. Some servers []. We may know, for example, that our customer John had connected to our New York VPN location on Tuesday and had transferred an aggregate of MB of data across a hour period. We encrypt all of the traffic between your device and our servers using TLS 1. Click on " Start Windows Fixup ". When you use Hotspot Shield to access the internet, we collect only anonymous, aggregate data about which websites you visit and which apps you use. Yes [28]. Virtual private network provider. We do not store any connection logs whatsoever. See also: Internet censorship in India. Benjamin Dowling, and Kenneth G. Archived from the original on April 14,

0 thoughts on “Vpn wikipedia”