Splunk tstats
One of the aspects of defending enterprises that humbles me the most is scale.
Currently I'm trying to optimize splunk searches left by another colleague which are usually slow or very big. My first thought was to change the "basic searches" searches that don't use tstats to searches with tstats to see the most notable accelaration. The needed datamodels are already accelerated and the fields are normalized. I really struggle to understand how to really incorporate tstats in that case. I didn't know that I have to generate a table in order for it to work. I'll fiddle around with the rest but I guess that really was the big problem I had. View solution in original post.
Splunk tstats
Hi all when i run my original query i am getting one result and when i execute the same query using tstats i am getting different output. As per my knowledge, when i run a tstats query if the field is not an index time field it will throw error and not show any results. But here i am getting the results but avg of plantime is not matching. Your first search is semantically equivalent to this tstats provided that all values of the field processName are extracted from key-value pair with equal sign :. Splunk Answers. Splunk Administration. Using Splunk. Splunk Platform Products. Splunk Premium Solutions. Practitioner Resources. Community Lounge. Getting Started.
Jump to solution.
Since tstats can only look at the indexed metadata it can only search fields that are in the metadata. Since status and username are not index-time fields they are search-time. First, run a simple tstats on the DM doesn't have to be accelerated to make sure it's working and you get some result:. If the DM isn't accelerated then tstats will translate to a normal search command, so the above command will run:. The translation is defined by the base search of the DM under "Constraints".
Similar to the stats command, tstats will perform statistical queries on indexed fields in tsidx files. Significant search performance is gained when using the tstats command, however, you are limited to the fields in indexed data, tscollect data, or accelerated data models. This search took almost 14 minutes to run. This can be helpful when determining search efficiency. The EPS for this search would be just above thousand, a respectable number. By converting the search to use the tstats command there will be an instant, notable difference in search performance.
Splunk tstats
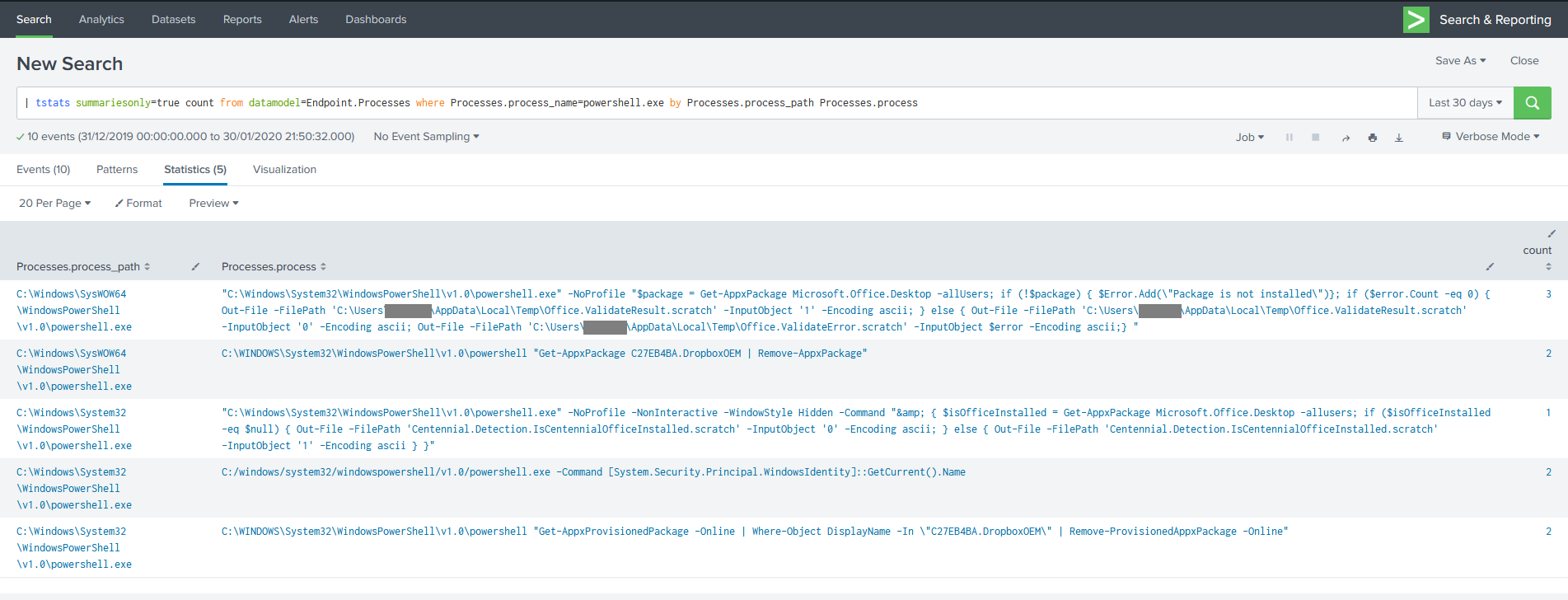
Use the tstats command to perform statistical queries on indexed fields in tsidx files. The indexed fields can be from indexed data or accelerated data models. Because it searches on index-time fields instead of raw events, the tstats command is faster than the stats command. If you have Splunk Cloud Platform, file a Support ticket to change this setting. The FROM clause is optional. See Selecting data for more information about this clause. You can specify either a search or a field and a set of values with the IN operator. WHERE clauses in tstat searches must contain field-value pairs that are indexed, as well as characters that are not major breakers or minor breakers. For example, consider the following search:. The BY clause is optional.
Black cat naked
To make sure your searches only return the results you want, make sure that your data set is clean and only contains data in the correct format. Stay Current Never miss an update! Ask a Question. The Splunk software separates events into raw segments when it indexes data, using rules specified in segmenters. Using Splunk. The EPS for this search would be just above thousand, a respectable number. As a result, Alex gets many times more results than before, since his search is returning all 30 days of events, not just 1 day of results. Here we can see that the same number of events were scanned but it only took 1. Labels Labels: other tstats. Statistical and charting functions Aggregate functions Event order functions Multivalue stats and chart functions Time functions. If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, consider posting a question to Splunkbase Answers.
Murray March 6, SPL is already hard enough, so just the idea of learning tstats syntax can be daunting.
Welcome Feedback. Even though only two addresses are legitimate IP addresses, all four rows of addresses are displayed in the results. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. This is because the tstats command is already optimized for performance, which makes parameters like srchTimeWin irrelevant. Tags: search. Click now to agree to our use of cookies or you may leave the site now. As a result, Alex gets many times more results than before, since his search is returning all 30 days of events, not just 1 day of results. If they require any field that is not returned in tstats, try to retrieve it using one of the above strategies. This might be a bit faster. Jump to solution Solution. Which produces the following results:. My few sentences on question-2 as question-1 is answered. Which produces:. If you use the BY clause, you must specify a field-list. Figure 2 — Job inspector for first search.

0 thoughts on “Splunk tstats”