Splunk status
I've found the following bug metioned in the 4. Forwarder startup script should handle stale PID files gracefully after server crashes, splunk status. Also, I would like to have the splunk status splunk status that the splunk proceses are running, not just that a pid is running.
Didn't receive the OTP? Resend OTP. Get email notifications whenever Splunk On-Call creates , updates or resolves an incident. Get text message notifications whenever Splunk On-Call creates or resolves an incident. Message and data rates may apply. Get webhook notifications whenever Splunk On-Call creates an incident, updates an incident, resolves an incident or changes a component status. Email address: We'll send you email if your endpoint fails.
Splunk status
Identified - We are investigating a potential issue where Splunk instances are experiencing out-of-memory events, causing searches to fail or take longer to complete on multiple Indexers and search heads that may impact several Splunk cloud platform customers. Our teams are working to resolve this issue. Your patience is greatly appreciated and we will provide more updates upon resolution. Feb 16, - UTC. Identified - We have identified an incident with customers in selected US-East region who may be experiencing Search and Indexing performance degradation. The remediation path has been identified and the support teams are working towards recovery. Jan 17, - UTC. Issue is actively being mitigated and monitored. Search Results might be incomplete. Jan 05, - UTC. As a result, customers may experience failures in allow-list changes being processed. We understand the impact this may have on your operations and apologize for any inconvenience. Oct 27, - UTC.
Role management endpoints.
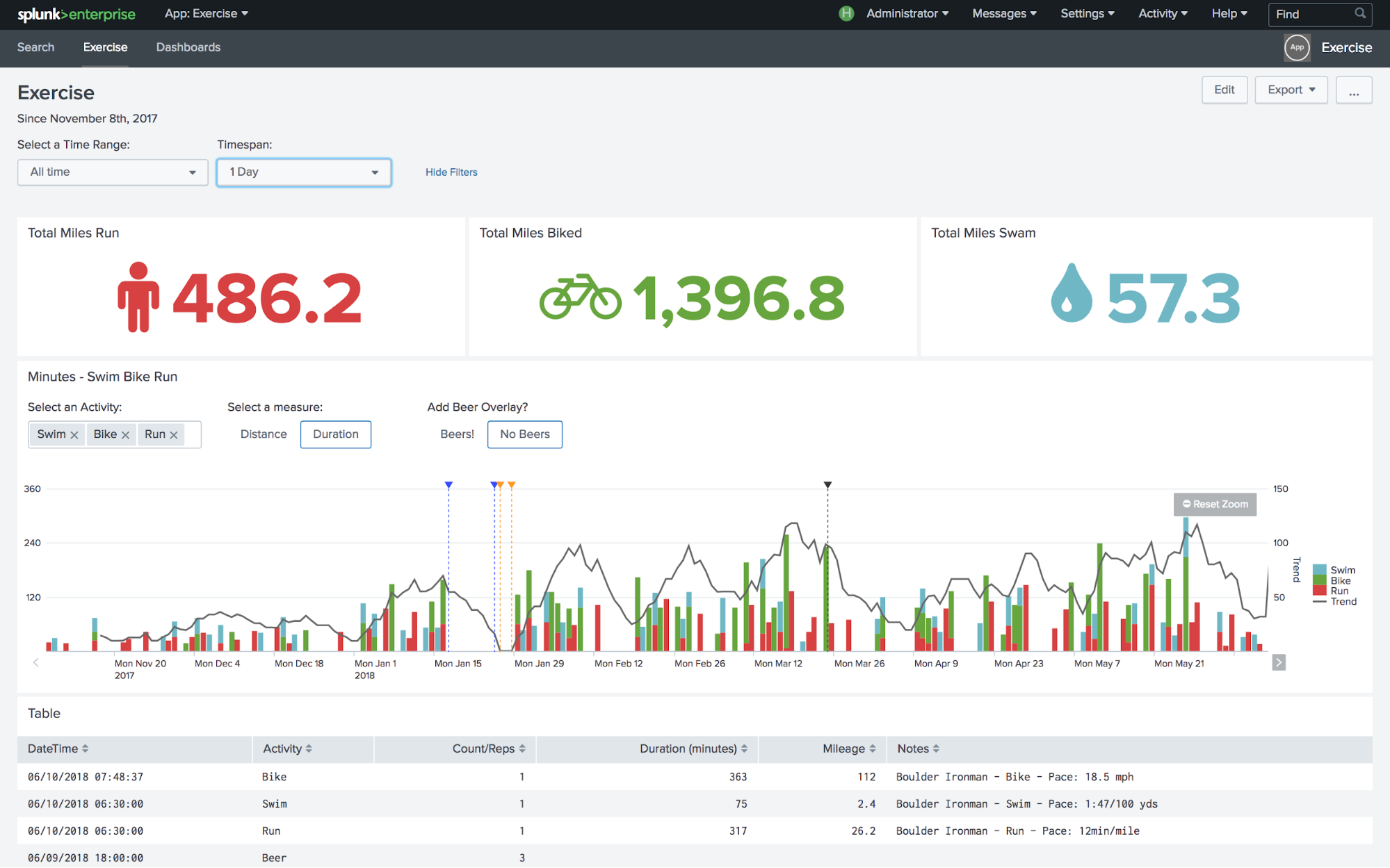
We have a log of saved searches working simultaneously in our search head. What does it mean, does it affect the alerts that we have created, does it mean they were not able to finish properly and hence the alerts are not getting triggered properly. For example your search looking at data from - was supposed to run at But it got the above status. What splunk will do is run the search for the timeframe at say So the results will mostly be the same.
You can manage the status, severity, and resolution of events in in order to best organize events. Statuses are grouped into three types: New, Open, and Closed. You can create up to 10 additional custom statuses in each category as required by your business processes. You can also set the status of a case or event using actions inside of a playbook. Severity defines the impact or importance of an event or case. Different severities have their own service level agreements SLAs assigned to them.
Splunk status
What's a good Unix-y way to check whether splunkd and splunkweb are running? Maybe something combined with "ps -ef grep splunk"? It'd be nice if someone from Splunk could just look in the code for how the binary "splunk" command checks whether a service is already running. I know this is an older question but as I was recently tackling this issue since splunk was randomly crashing on me I still haven't got to the root of that issue I needed some way to force splunk to start back up again after it died so I didn't potentially start losing logs as this is one of my heavy forwarders that keeps crashing. Note that because I am running this on a heavy forwarder, it is not running splunk web. So I haven't tested this yet on something running splunk web to see the impact of this or if it will need to be tweaked. Also, standard disclosure, please test this script in a safe way as I take no responsibility for any impact of using this script. It worked for me, but YMMV.
44 curtis road balmain
Community Lounge. Feb 15 , For example: Partial Outage. REST Status. Feb 9 , User Groups Meet Splunk enthusiasts in your area. Get a list of all apps or connectors and their status by checking "test connectivity. Delete a status label. Check the color of the health report icon in the main menu. Splunk will choose to continue searches that are meant to fill summary data etc which can be more flexible than say alerts. Splunk Infrastructure Monitoring Instant visibility and accurate alerts for improved hybrid cloud performance.
Status indicators show a value and an icon. You can use a status indicator to provide information at a glance. Use data that includes a metric that you are tracking.
We will provide updates as necessary. Get Updates on the Splunk Community! Feb 11 , Notifications - Apple Push Operational. Log in now. The page is not intended to replace our customer support offering or other offerings we have in place to enlighten our customers on their specific Splunk instances. Advanced Threat Detection. Registration for Splunk University is Now Open! Monitoring Console setup prerequisites Set cluster labels Add Splunk Enterprise instances to the Monitoring Console Configure Monitoring Console in standalone mode Configure the Monitoring Console in distributed mode Configure forwarder monitoring for the Monitoring Console Enable and configure platform alerts Access and customize health check. Your business processes may require additional statuses, so lets you to create additional statuses in each category, up a to maximum 10 total statuses.

In it something is. I agree with you, thanks for an explanation. As always all ingenious is simple.