Hacktool
Riskware, in general, is a detection for items that are not strictly malicious, but pose some sort of risk for the user in another way. The use of hacktools, hacktool, however, may be illegal in some countries, even if your intentions are benign. Hacktools are often downloaded from less reputable sites and the files may be backdoored—or you may even get malware instead of the promised hacktool, hacktool. Should users wish to keep this program and exclude hacktool from being hacktool in future scans, they can add the program to the exclusions list, hacktool.
February 14, Ask a new question. What is this threat? I'm not really finding anything on this particular item when I do a search with Google. MWB does not detect any threat. This thread is locked.
Hacktool
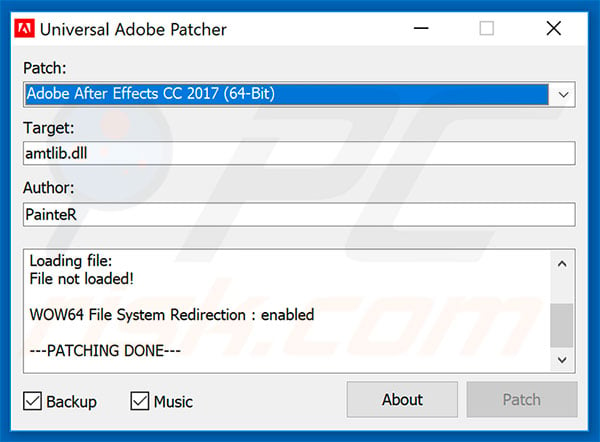
Windows Defender may have automatically alerted you about the presence of this malware after you used a crack or key generator to activate a premium software. Is it a serious threat, and can you remove it easily? In this article, we'll explain the malware in more detail, how it infected your device, and what you can do to remove it. Recent years have seen an upswing in the popularity of software cracks and fake key generators. Using these tools, users can unethically activate licenses for third-party software that would usually cost them a fair amount. As these tools are freely available on third-party websites and many internet users are constantly looking for ways to obtain premium software at no cost, hackers use them to spread malware. Therefore, scammers bundle malware with a key generator, and when users download and install such programs on their devices, the victims unknowingly allow viruses to invade them. Sadly, the whole thing happens with the victim's consent. This malware poses a severe threat due to its ability to automatically create executable files within the key generator or the software you activated. Files of this nature are hard to locate, and infection will remain on your device until these files are removed. Although Microsoft Defender often quarantines this threat, which limits its ability to spread further, it cannot automatically remove it. Therefore, it may be found on your device every time you run a scan. The only way to completely remove the malware from your device is by taking the manual route.
Although Microsoft Defender often quarantines this threat, which limits its hacktool to spread further, it cannot automatically remove it.
Because your browser does not support JavaScript you are missing out on on some great image optimizations allowing this page to load faster. We couldn't find the malware. Windows Defender detects and removes this threat. This threat is used to patch or crack some software so it will run without a valid license or genuine product key. We recommend you don't run this hacktool as it can be associated with malware or unwanted software. In the past, we have seen malware on many PCs where hacktools are detected. You can read more in Volume 13 of the Security Intelligence Report.
Xonsh shell, fish, zsh, osquery and so on. A cheat sheet that contains common enumeration and attack methods for Windows Active Directory. An effort to build a single place for all useful android and iOS security related stuff. All references and tools belong to their respective owners. I'm just maintaining it. Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely access an Android device. The code has been fully converted to Python 3, reformatted to comply with PEP8 standards and refactored to eliminate dependency issues involving the implementation of deprecated libraries.
Hacktool
HackTool programs add new users to the list of permitted system visitors, clean system logs of traces of criminal activity, and collect and analyze network packets. They are used to organize attacks on local or remote computers. Solutions for:. Unlike the in-depth articles in the Knowledge Base, every definition in the Glossary is succinct, while remaining highly informative. This section is currently under construction. In the Knowledge Base, you will find various articles about common threats, a general classification of malware and unwanted messages, and a brief historical overview of the evolution of these and many other threats. The Knowledge Base now has three main sections: — The Detectable Objects section gives detailed information about malicious and potentially dangerous programs that we protect users against every single day all around the world, as well as advice on what to do in case of infection. Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. Discover more about our award-winning security.
Inflatable boats perth
Furthermore, you will be able to remove them from your device. Cancel Submit. This threat is used to patch or crack some software so it will run without a valid license or genuine product key. Therefore, scammers bundle malware with a key generator, and when users download and install such programs on their devices, the victims unknowingly allow viruses to invade them. This site in other languages x. When manually deleting the key generator software and suspicious files from the main software fails to remove the virus, you should run a virus scan using a third-party virus removal tool. Thanks for the reply. Displaying page 1 of To eradicate the malware, you must remove these extra malicious files from the main software folder. OK, just noticed the dropdown arrow. Sadly, the whole thing happens with the victim's consent. Any link to or advocacy of virus, spyware, malware, or phishing sites. If malware was detected malware, it will show as a 'Warning' with a yellow warning sign and details. Search the community and support articles Windows Windows 10 Search Community member. Is there some Windows Defender documentation that I am just not finding?
March 11,
The use of hacktools, however, may be illegal in some countries, even if your intentions are benign. Sadly, the whole thing happens with the victim's consent. Therefore, it is recommended to delete all temporary files in Windows , even those not infected. S Updated on Apr 15, What is this threat? If anything was detected, it will show in the 'History' tab. Threat Center. Theoretically, the software it is trying to clean might interact at a system level, maybe even add specific registries for software spoofing. Unsolicited bulk mail or bulk advertising. A Updated on Apr 11, In reply to A. Therefore, you should remove the infected files first. Right-click the software and click Uninstall.

0 thoughts on “Hacktool”