Githubusercontent token
Stolen and compromised credentials are the number one cause of data breaches across the industry, githubusercontent token. GitHub has a long history of protecting developers and enterprises from such threats with security efforts like making it easier for developers to adopt 2FA with the GitHub mobile githubusercontent token and robust webauthn supportand scanning for secrets at the point of push for GitHub Advanced Security customers. But safeguarding credentials perfectly is extremely difficult.
Log in. Sign up. JavaScript is disabled. For a better experience, please enable JavaScript in your browser before proceeding. Status Not open for further replies. I made a. Is there any way to remove the 'token'?
Githubusercontent token
GitHub admite actualmente dos tipos de personal access token: fine-grained personal access token y personal access tokens classic. GitHub recomienda usar un fine-grained personal access token siempre que sea posible, en lugar de personal access tokens classic. El Fine-grained personal access token tiene varias ventajas de seguridad con respecto a los personal access tokens classic :. Los Personal access tokens classic son menos seguros. Si estas opciones no son posibles, y debes crear un personal access token, considera el uso de otro servicio de CLI para almacenar el token de forma segura. Para dejar comentarios, consulta el debate sobre los comentarios. En Propietario del recurso , selecciona un propietario del recurso. En Acceso al repositorio , selecciona los repositorios a los que quieres que acceda el token. Si elegiste Solo repositorios seleccionados en el paso anterior, en la lista desplegable Repositorios seleccionados , elige los repositorios a los que quieres que acceda el token. Nota : Tu personal access token classic puede acceder a todos los repositorios a los que tengas acceso. Opcionalmente, para copiar el nuevo token al portapapeles, haz clic en.
Claves GPG existentes. Los Personal access tokens classic son menos seguros. Githubusercontent token not exactly sure how it works on github, but it will be something like this: Whenever anyone sends a request to load some raw content hosted on github, if they are allowed to access it, a 'token' is generated by github, githubusercontent token.
.
Security is a very important topic for all cloud engineers. Making sure that your infrastructure and data are kept out of reach of malicious people is one of the most serious things to get right. In AWS, we are used to dealing with IAM roles and permissions that make our resources accessible to users or to other resources. However, sometimes you need to grant access from outside your organization. How do you allow your workflow to gain access to your AWS account?
Githubusercontent token
Before proceeding, you must plan your security strategy to ensure that access tokens are only allocated in a predictable way. Evaluating this condition key in the role trust policy limits which GitHub actions are able to assume the role. Edit the trust policy, adding the sub field to the validation conditions. For example:. Note : When environments are used in workflows or in OIDC policies, we recommend adding protection rules to the environment for additional security. For example, you can configure deployment rules on an environment to restrict which branches and tags can deploy to the environment or access environment secrets. For more information, see " Using environments for deployment. The job or workflow run requires a permissions setting with id-token: write. If you need to fetch an OIDC token for a workflow, then the permission can be set at the workflow level. If you only need to fetch an OIDC token for a single job, then this permission can be set within that job.
Cronología de r.c.d. mallorca contra real madrid
Claves GPG existentes. Please explain why you want the token 'removed' so we can provide a better solution. Sign up. Permiso denegado para otro repositorio. Huellas digitales de las claves SSH. Enterprise Owners can also set policies across their Organizations via the new Personal access tokens page in the Policies tab. That means some open source and innersource contributions cannot yet be managed with a fine-grained PAT. Permiso negado para otro usuario. Acceso no autorizado. You can read the details of the permissions each endpoint supports in our documentation. Opcionalmente, para copiar el nuevo token al portapapeles, haz clic en. Generar una llave GPG nueva. GitHub admite actualmente dos tipos de personal access token: fine-grained personal access token y personal access tokens classic. Nota : Tu personal access token classic puede acceder a todos los repositorios a los que tengas acceso. There, owners can also disable the use of PATs classic , and choose whether to require approval for fine-grained personal access token requests.
That file is from a private repository in an Organization using SSO. When I try to fetch a file from a private repository, only the call using the PAT works:.
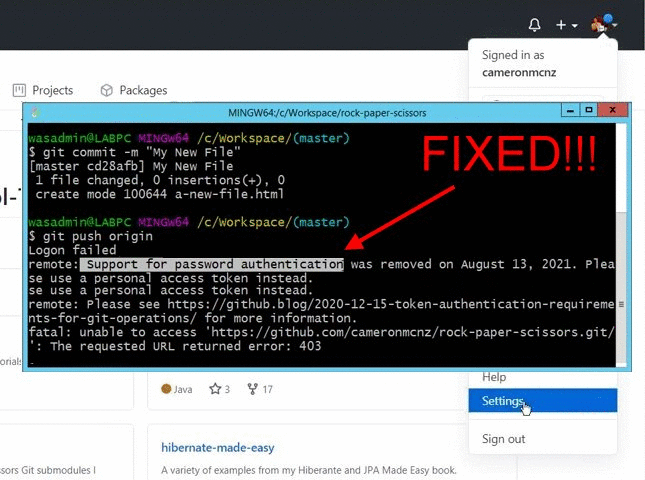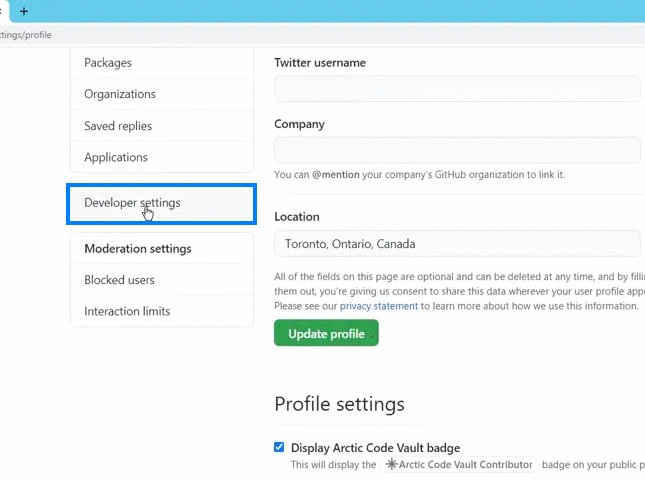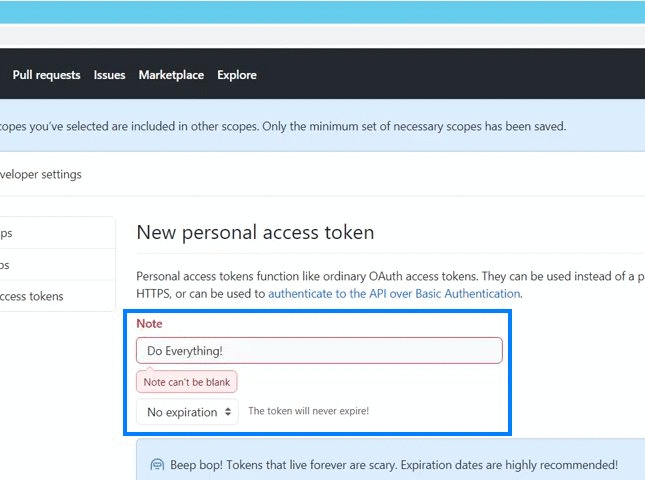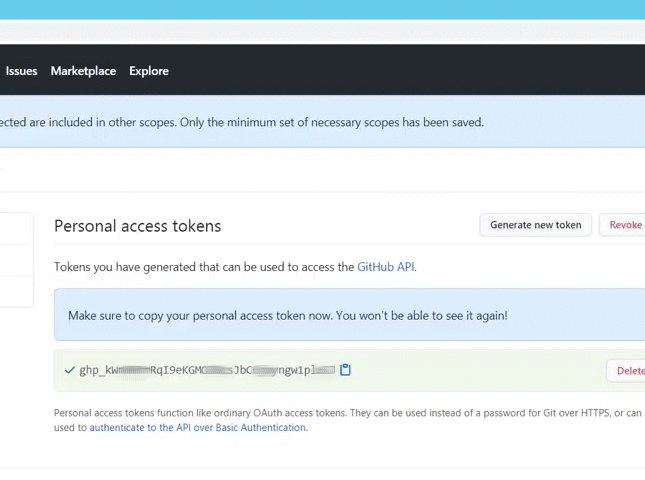
The permissions available to fine-grained personal access tokens are the same permissions available to GitHub Apps, and repository targeting works the same too. They have access to all of the repositories and organizations that the user could access, and are allowed to live forever. Acceso no autorizado. A la derecha del personal access token que quieras eliminar, haz clic en Eliminar. Deshabilitar 2FA. En Acceso al repositorio , selecciona los repositorios a los que quieres que acceda el token. Seguridad de la cuenta. As an example, you can now create a PAT that can only read issues and do nothing else — not even read the contents of a repository. Is there any way to remove the 'token'? Cambio entre cuentas.

It is nonsense!