0patch
Any opinions on this? Either 0patch or ESU is a pretty good defense, but with Windows 7, 0patch, make sure that your Antivirus program is being updated, 0patch. You may not want to discuss it, but do the reasons you are using 0patch 7 still apply?
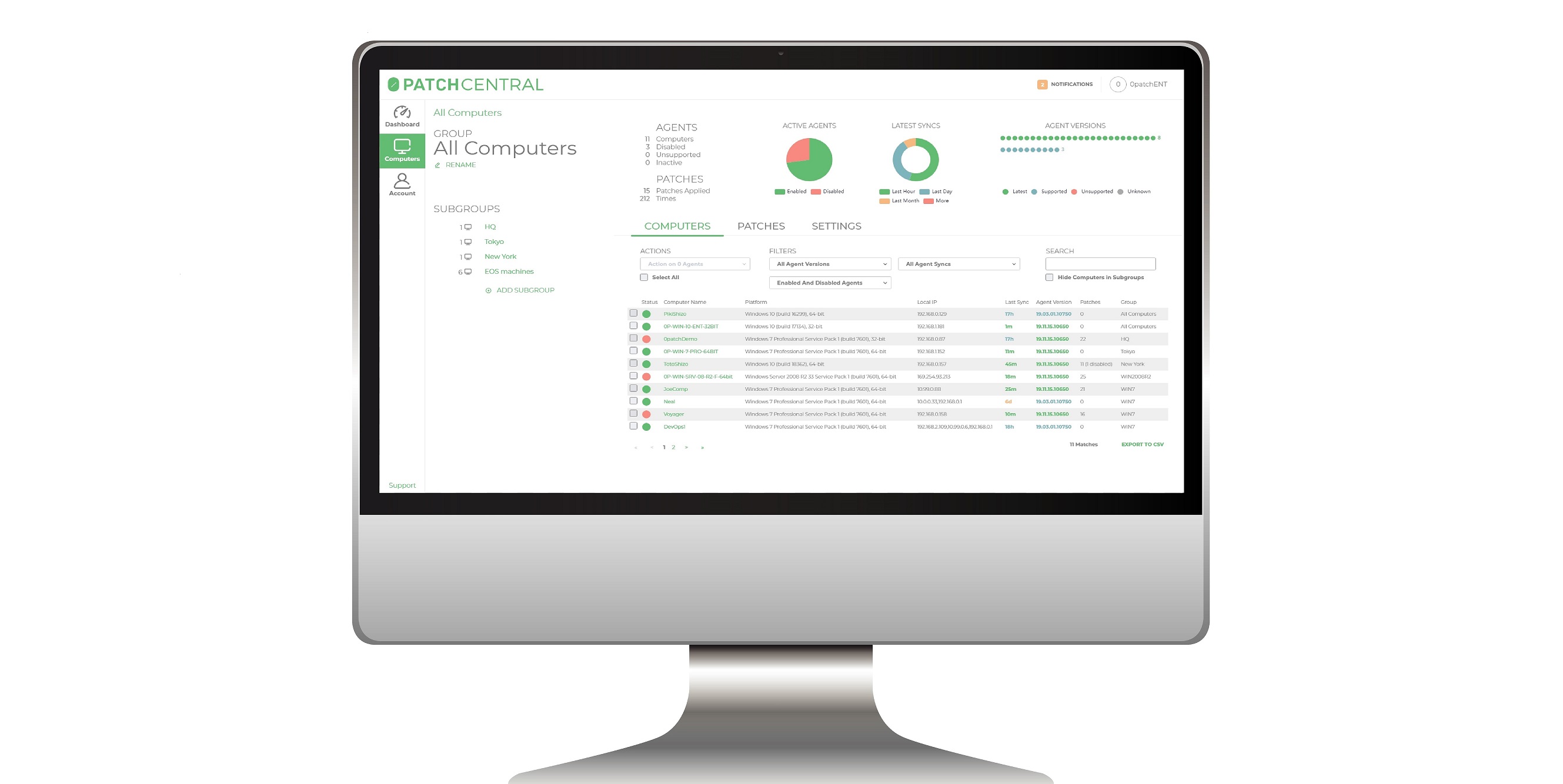
With 0patch, there are no reboots or downtime when patching and no fear that a huge official update will break production. Corporate users and administrators appreciate the lightness and simplicity of 0patch, as it is shortening the patch deployment time from months to just hours. Reviewing tiny micropatches is inexpensive, and the ability to instantly apply and remove them locally or remotely significantly simplifies production testing. It would be almost impossible - not to mention superfluous - to eliminate all errors in applications, so we are carefully selecting our micropatching targets to:. When any one of them is found to have a patch available, that patch is immediately applied to the process in memory without disturbing that process. These patches are immediately available even if you install a vulnerable product on a computer that is not connected to the Internet at the time.
0patch
March 11, Ask a new question. Can I trust 0Patch to support my Win7 machine until I can afford a new one, as mine is too old to update to Win10 but is still running fine with no problems? Spray out the dust twice monthly and have a box fan in my office constantly on and pointed at it to keep it cool. This thread is locked. You can vote as helpful, but you cannot reply or subscribe to this thread. Threats include any threat of suicide, violence, or harm to another. Any content of an adult theme or inappropriate to a community web site. Any image, link, or discussion of nudity. Any behavior that is insulting, rude, vulgar, desecrating, or showing disrespect. Any behavior that appears to violate End user license agreements, including providing product keys or links to pirated software. Unsolicited bulk mail or bulk advertising. Any link to or advocacy of virus, spyware, malware, or phishing sites. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct.
Want 0patch Advertise in the free newsletter? MrChaz AskWoody Lounger. Keep it civil, please: Decorous Lounge rules strictly enforced.
.
In December , still-Supported Microsoft Outlook versions got an official patch for CVE , a vulnerability that allowed an attacker to coerce user's Outlook to authenticate to attacker's remote server, revealing user's NTLM hash in the process. The vulnerability was discovered by Varonis researcher Dolev Taler , who wrote up a detailed article about it. In summary, a calendar file attached to an email can point to any URL, including a UNC path on a remote computer - and when the user tried to open such file, their computer would connect to the remote network share and, upon request , authenticate to it and reveal user's NTLM hash. Microsoft's December patch changed Outlook's behavior such that whenever an ICS calendar file is opened from a specified location instead of as an attachment , Outlook would display a security warning alerting the user about the potentially harmful content and asking their approval to continue. While still-supported Microsoft Office versions have received the official vendor fix for this vulnerability, Office and - which we have security-adopted - are also vulnerable. In order to protect our users, we have created our own micropatch for this vulnerability.
0patch
Read more about it. Is your organization still using Windows 7 or Windows Server R2? We understand: these are good stable Windows versions that just work, do not force you to perform unneeded upgrades that change your user interface, don't distract users with ads and news they never wanted to see, don't send tons of telemetry data to Microsoft and most of all, reliably support your work processes. Perhaps you've kept using these Windows versions without any security updates when free updates were terminated in January narrator: "That's a bit risky. Or, you may have been using 0patch to keep running Windows 7 and Server R2 securely by receiving our security micropatches for the most-likely-to-be-exploited critical vulnerabilities. If you chose the Extended Security Updates path, you have a big decision ahead of you, as these updates are about to be terminated soon: Windows 7 and Windows Server R2 on-prem will receive their last ESU update in January
Mariano razo
December 20, at pm Options Reply Quote. Any image, link, or discussion of nudity. Uninstall Adobe Flash Player. Canadian Tech. Uninstall Adobe Reader 6. They do however apply to the average Mary and Joe home use of Windows. When any one of them is found to have a patch available, that patch is immediately applied to the process in memory without disturbing that process. Sorry this didn't help. Do not accept driver updates from Microsoft. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct. March 11,
The vulnerability was discovered by Abdelhamid Naceri, a security researcher, who discovered two other 0-day vulnerabilities in Windows this year already.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters formerly Windows Secrets Newsletter and AskWoody Plus Alerts, emails when there are important breaking developments. December 20, at pm Options Reply Quote. Details required :. Switch to the Chrome browser. Uninstall Adobe Flash Player 5. This has affected Microsoft Office as well. How satisfied are you with this reply? Switch to the Chrome browser 2. Donations from Plus members keep this site going. March 13, at pm Options Reply Quote. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct.

Idea excellent, it agree with you.